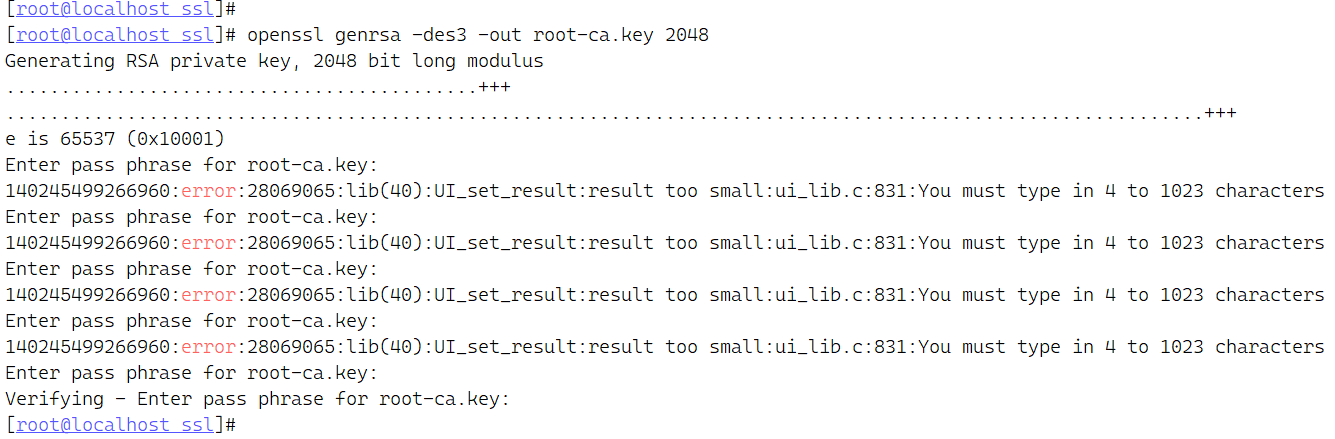
零、 生成 CA 私钥 openssl genrsa -des3 -out root-ca.key 2048
由于是根CA的私钥,这里系统要求一定要输入密码 也有可能是des3算法的原因,没有具体测试
一、 生成 CA 证书 1.1 非交互式回答CSR信息 openssl req -x509 -new -nodes -sha256 -days 7300 \ -key root-ca.key \ -out root-ca.crt \ -subj "/C=CN/ST=Zhejiang/L=Hangzhou/O=root/OU=root/CN=root"
参数含义
C : Country Name ST :State or Province Name L :Locality Name O :Organization Name OU :Organizational Unit Name CN :Common Name
1.2 交互式应答生成 openssl req -x509 -new -nodes -sha256 -days 7300 -key root-ca.key -out root-ca.crt
交互式生成CSR要求留email地址
[root@localhost CA]# openssl req -x509 -new -nodes -sha256 -days 720 -key root-ca.key -out root-ca.crt \ > Enter pass phrase for root-ca.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:Zhejiang Locality Name (eg, city) [Default City]:Hangzhou Organization Name (eg, company) [Default Company Ltd]:root Organizational Unit Name (eg, section) []:root Common Name (eg, your name or your server's hostname) []:root Email Address []:@root.com [root@localhost CA]#
1.3 查看证书 openssl x509 -in root-ca.crt -noout -text
[root@localhost CA]# openssl x509 -in root-ca.crt -noout -text Certificate: Data: Version: 3 (0x2) Serial Number: 83:6d:15:68:11:48:42:af Signature Algorithm: sha256WithRSAEncryption Issuer: C=CN, ST=Zhejiang, L=Hangzhou, O=root, OU=root, CN=root Validity Not Before: Sep 21 17:46:03 2023 GMT Not After : Sep 16 17:46:03 2043 GMT Subject: C=CN, ST=Zhejiang, L=Hangzhou, O=root, OU=root, CN=root Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:d9:6c:a1:a7:2c:a4:d1:32:3a:c3:40:63:7f:5e: 79:20:4f:cc:1e:99:e2:38:98:e8:e1:64:7c:39:7d: b9:ed:10:20:d5:06:7f:27:13:bf:b8:07:fc:9a:48: 01:21:a0:6b:7b:ae:4e:be:8f:f2:43:02:8c:5e:14: 56:cf:8b:fa:e0:6e:5f:1c:5c:4e:d7:3a:17:b2:f7: 58:aa:ef:4c:6b:e4:cd:38:cf:92:7e:15:e5:52:66: c2:b1:47:4d:2e:74:49:a9:4a:bc:1e:60:c2:48:7d: 6b:16:c5:34:46:23:2c:3c:dc:19:f0:d5:ba:a8:b7: 43:3b:7f:a0:65:21:26:78:0d:de:96:60:c7:58:50: 64:bd:7c:9d:8b:68:55:f7:d2:ed:40:ad:b7:f1:50: e2:9d:ac:e6:a3:b6:0e:4d:12:ab:50:54:5b:3e:62: 68:ad:6f:dd:8f:50:b5:20:25:28:46:4d:24:42:99: c1:ae:60:08:42:c6:40:aa:e1:3c:fc:59:ce:17:39: a9:b2:54:6b:fb:62:f0:11:4e:91:45:e9:6a:90:b6: e6:ab:27:82:50:3b:b2:66:44:47:0e:73:1d:cd:65: 4c:c8:c8:3c:f7:b1:2c:ff:2a:55:c7:90:be:14:17: 24:2b:05:69:18:fd:51:23:28:39:6a:3c:7b:52:e9: cb:4b Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Subject Key Identifier: A0:6F:B7:44:0F:E4:57:9C:B0:64:72:EE:00:BE:D1:D7:D6:BA:E2:F5 X509v3 Authority Key Identifier: keyid:A0:6F:B7:44:0F:E4:57:9C:B0:64:72:EE:00:BE:D1:D7:D6:BA:E2:F5 X509v3 Basic Constraints: CA:TRUE Signature Algorithm: sha256WithRSAEncryption 0c:66:dc:ea:7d:ad:84:d2:a2:a2:1e:76:87:d3:14:62:85:1d: 63:f4:d0:2d:a7:5b:3c:42:24:45:21:85:d6:d1:29:02:aa:4d: 8b:21:1d:10:13:7a:dd:b6:c7:fd:2a:68:44:85:3a:62:86:2d: db:31:34:64:d6:c2:44:a3:78:18:85:ba:24:fe:ce:ed:f1:9a: 25:90:76:da:f8:10:b1:67:f8:b0:35:47:a2:1d:5d:88:f5:d8: 5a:c7:34:36:06:bd:4d:eb:db:6c:39:4d:56:9c:7a:8f:0e:19: e6:97:43:5d:87:ca:79:52:e8:be:eb:3e:08:a3:d6:17:22:b3: d9:ff:67:ef:1f:43:28:b1:4c:c7:d1:7f:fa:0b:b5:2c:65:47: ed:16:cd:07:f0:1d:15:64:5e:c6:74:9c:b8:78:59:a6:1f:07: 3a:ec:1c:54:d4:18:33:bc:00:b5:5b:f3:25:87:4d:63:d8:dd: 37:e6:88:a1:e8:9e:49:0f:88:cf:5e:d0:73:68:84:fe:8e:3c: b6:05:fb:51:3b:e9:62:e8:43:2c:e4:ed:83:85:43:86:f7:ee: f8:52:b7:26:ae:6a:58:ed:69:9a:78:a7:9c:0a:49:1d:7e:38: 31:e5:a0:21:ab:cb:2a:85:59:7a:97:29:7e:96:06:c9:93:75: 15:83:74:88 [root@localhost CA]#
二、 生成 ssl 私钥 openssl genrsa -out mdzz.wang.key 2048
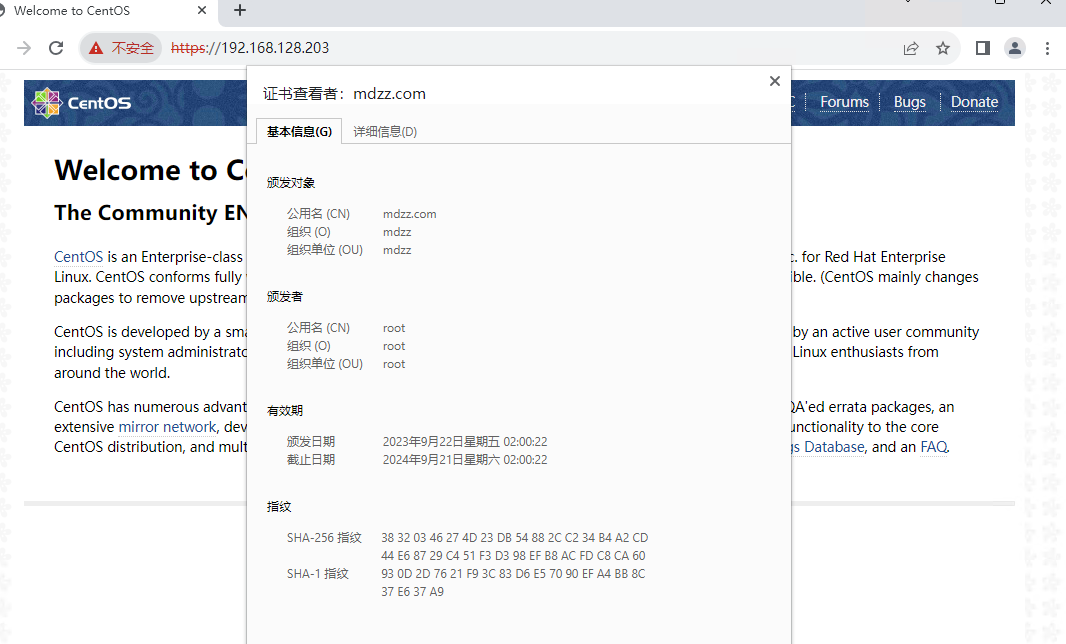
三、 生成 签名请求 openssl req -new -key mdzz.wang.key -out mdzz.wang.csr -subj "/C=CN/ST=Zhejiang/L=Hangzhou/O=mdzz/OU=mdzz/CN=mdzz.wang"
四、 域名附加配置文件 vim cert.ext
authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment subjectAltName = @alt_names [alt_names] DNS.1 = localhost IP.2 = 127.0.0.1 DNS.3 = mdzz.com DNS.4 = *.mdzz.com
五、 CA 签署ssl证书 openssl x509 -req -in mdzz.wang.csr -out mdzz.wang.crt -days 365 \ -CAcreateserial -CA root-ca.crt -CAkey root-ca.key \ -CAserial serial -extfile cert.ext
5.1 查看证书 总结
创建CA机构 创建CA密钥 生成CA证书 为网站mdzz.wang创建https私钥 为网站mdzz.wang生成CSR请求文件 使用CA为mdzz.wang颁发证书
六、 快速构建https证书 某些情况只需要配置https证书, 不要受信任的CA签名的时候
6.1 生成私钥 openssl genrsa -des3 -out test.key 2048需要输入根证书的密码
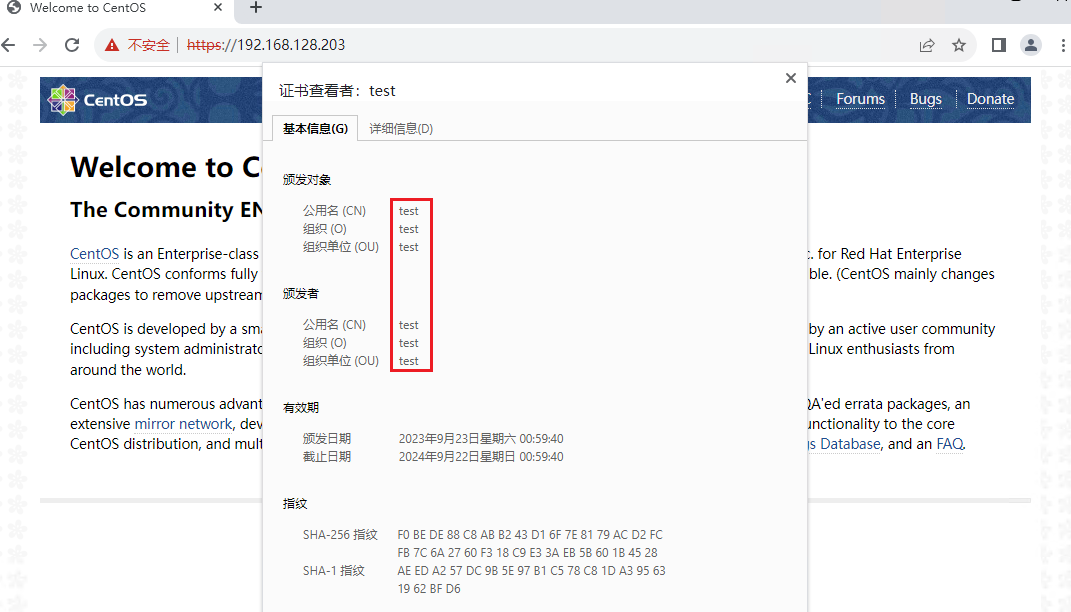
6.2 使用私钥自签证书 openssl req \ -newkey rsa:2048 -nodes -keyout test.key \ -x509 -days 365 -out test.crt \ -subj "/C=CN/ST=Zhejiang/L=Hangzhou/O=test/OU=test/CN=test"
6.3 证书验证